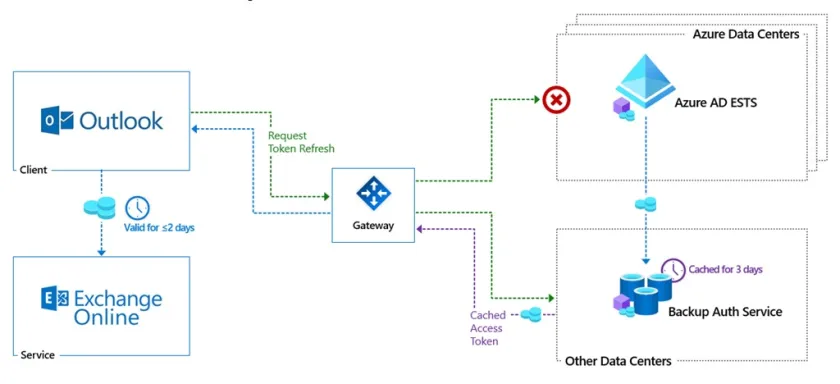
MFCMAPI is a widely used troubleshooting and diagnostic tool that provides deep insight into Outlook and Exchange mailbox data using the Messaging API (MAPI). As organizations shift toward more secure authentication protocols, the question of whether MFCMAPI supports Modern Authentication (OAuth 2.0) has become increasingly important for IT professionals and administrators.
Modern Authentication, which leverages OAuth protocols, is now the standard across Microsoft 365 and Exchange Online due to the deprecation of Basic Authentication. Understanding how MFCMAPI interacts with this newer model is essential for secure mailbox access, particularly in environments that have disabled legacy authentication methods.
Understanding Modern Authentication (OAuth 2.0)
As cloud services and security standards evolve, so do the mechanisms used to authenticate users and applications. Modern Authentication represents a shift away from traditional, less secure methods of authentication toward more robust, flexible, and secure protocols. In the Microsoft ecosystem, Modern Authentication is primarily based on OAuth 2.0 and is supported by components such as ADAL (Active Directory Authentication Library) and MSAL (Microsoft Authentication Library). This approach is foundational to accessing Microsoft 365, Exchange Online, and other Azure-integrated services.
What Is Modern Authentication?
Modern Authentication is an umbrella term used by Microsoft to describe the use of OAuth 2.0-based authentication and authorization protocols to access services like Exchange Online, SharePoint Online, and Teams. It enables applications to securely obtain access tokens on behalf of users or services, without transmitting or storing passwords directly.
At its core, Modern Authentication introduces token-based authentication, in contrast to the older username and password model. When a user or application authenticates through Modern Authentication, they are issued access tokens and refresh tokens, which are used to communicate securely with Microsoft services.
This method of authentication allows organizations to leverage features like:
- Single Sign-On (SSO)
- Multi-Factor Authentication (MFA)
- Conditional Access Policies
- Smart card and biometric-based authentication
These capabilities significantly increase both the flexibility and the security of user and application authentication across Microsoft services.
Key Components of Modern Authentication
Modern Authentication relies on a set of technologies and protocols, the most important of which are:
OAuth 2.0 (Open Authorization)
OAuth 2.0 is an industry-standard protocol for authorization. It enables users to grant applications limited access to their resources without revealing their credentials. Instead of sending a username and password to every application, OAuth 2.0 allows the user to authenticate once through a trusted identity provider (such as Azure Active Directory), which issues tokens that the app can use to access resources.
In Microsoft environments, OAuth 2.0 is the backbone of Modern Authentication, allowing secure token-based access to Exchange Online, Graph API, SharePoint, and more.
ADAL (Active Directory Authentication Library)
ADAL is Microsoft’s legacy library that provides support for OAuth 2.0 authentication flows. It was widely used by earlier versions of Microsoft applications to acquire tokens from Azure Active Directory. While ADAL served its purpose for years, Microsoft has since deprecated it and replaced it with a more advanced and flexible library, MSAL.
MSAL (Microsoft Authentication Library)
MSAL is the newer and recommended library for integrating authentication into applications that need to communicate with Microsoft identity platforms. It supports multiple identity providers, broader platform coverage, and enhanced security features. MSAL simplifies the implementation of OAuth 2.0 flows and token management while supporting all modern capabilities, including:
- Azure AD B2C
- Account switching
- Identity federation
- Device code authentication
MSAL is the cornerstone of new applications that need to perform Modern Authentication in the Microsoft ecosystem.
How Modern Authentication Differs from Basic Authentication
Understanding the differences between Modern Authentication and Basic Authentication is crucial for appreciating the significance of this shift in Microsoft services.
Basic Authentication Overview
Basic Authentication is the traditional method where a user provides a username and password, which are then sent with each request to the server. This method has several serious limitations:
- Passwords are transmitted and stored frequently, increasing exposure to interception or misuse.
- It lacks support for modern security features like MFA or conditional access.
- It is vulnerable to brute-force and phishing attacks.
- There’s no token reuse—credentials are needed for each session.
In contrast, Modern Authentication was designed to overcome these vulnerabilities.
Key Differences
- Credential Exposure:
- Basic Auth: Credentials are transmitted with every request.
- Modern Auth: Tokens are used instead of passwords, reducing the risk of credential leakage.
- Security Enhancements:
- Basic Auth: No support for MFA or device compliance checks.
- Modern Auth: Integrates seamlessly with MFA, biometric login, and conditional access.
- Session Management:
- Basic Auth: Lacks session control; once credentials are compromised, access is open.
- Modern Auth: Tokens have expiration times and can be revoked or refreshed securely.
- User Experience:
- Basic Auth: Users are prompted for credentials frequently.
- Modern Auth: Single sign-on capabilities mean users log in once and gain access across services.
- Compliance & Auditing:
- Basic Auth: Offers minimal visibility and control over authentication.
- Modern Auth: Detailed audit trails and policy-based access controls support compliance needs.
Why Microsoft Is Enforcing OAuth and Deprecating Basic Authentication
The shift from Basic Authentication to Modern Authentication is not just a technical improvement—it’s a necessary evolution in response to the increasing sophistication of cybersecurity threats. Microsoft has announced and enforced the retirement of Basic Authentication across several services, particularly Exchange Online, for several compelling reasons:
Security
Basic Authentication is inherently insecure. Since it transmits usernames and passwords with every request, it becomes an easy target for man-in-the-middle (MITM) attacks, credential stuffing, and brute-force attacks. Once credentials are compromised, attackers can gain unrestricted access to sensitive data.
Modern Authentication, powered by OAuth 2.0, minimizes these risks through tokenization, encrypted sessions, and limited scopes for access tokens. It also supports MFA, making unauthorized access significantly more difficult.
Conditional Access and Policy Enforcement
Modern Authentication integrates with Azure AD’s Conditional Access, allowing organizations to define policies based on user location, device health, risk level, and more. Basic Authentication lacks this granularity, making it unsuitable for enterprise-grade access management.
With OAuth 2.0, administrators can enforce:
- Location-based restrictions
- Device compliance checks
- Time-based access controls
- Application-specific access scopes
This leads to more precise and secure access management across cloud and hybrid environments.
Compliance and Governance
Regulatory standards like GDPR, HIPAA, ISO 27001, and others require strong access control mechanisms, data encryption, and auditability. Basic Authentication does not offer sufficient controls or auditing capabilities to meet these requirements.
Modern Authentication provides:
- Detailed logging and audit trails
- Token lifetimes and revocation capabilities
- Centralized identity governance through Azure AD
These features help organizations stay compliant and reduce risk.
Improved User Experience
Modern Authentication significantly improves the user experience through features like Single Sign-On (SSO) and Seamless Sign-In. This reduces login prompts, increases productivity, and minimizes the need for password resets.
In contrast, Basic Authentication often results in repeated login prompts and degraded user satisfaction.
Scalability and Future-Proofing
Modern Authentication is designed for modern applications—mobile, desktop, and web-based. It supports API access, delegated permissions, and automation securely. Microsoft’s long-term roadmap depends entirely on token-based authentication models like OAuth.
By deprecating Basic Auth, Microsoft ensures all future development aligns with cloud-first, secure-by-design principles.
MFCMAPI and Authentication Methods
Understanding how MFCMAPI handles authentication is essential for professionals working with Outlook, Exchange Server, or Microsoft 365 environments. As Microsoft continues its transition away from Basic Authentication to Modern Authentication (OAuth 2.0), many administrators and support personnel need clarity on how tools like MFCMAPI interact with these evolving protocols.
Default Authentication Behavior of MFCMAPI
MFCMAPI is not a standalone email client—it functions as a low-level interface to the MAPI subsystem provided by Microsoft Outlook. Because of this design, MFCMAPI itself does not manage authentication directly. Instead, it relies entirely on the MAPI profile configured in Outlook to establish mailbox connections.
When a user launches MFCMAPI and selects a profile, it utilizes the authentication and session state already maintained by Outlook or Exchange. This means MFCMAPI does not prompt for credentials, nor does it initiate any login sequence on its own. Its role is to interact with a session that’s already authenticated via Outlook.
This behavior is by design, ensuring that MFCMAPI remains a passive and non-intrusive tool—ideal for diagnostics, but limited when it comes to modern, token-based authentication requirements.
Support for Legacy Authentication Protocols
Historically, MFCMAPI worked seamlessly in environments where Basic Authentication was enabled. Basic Authentication refers to the traditional model where users log in with a username and password. Once credentials were validated, MAPI sessions were initiated and maintained.
This legacy model was simple and widely adopted. For years, MFCMAPI could access on-premises Exchange servers or Exchange Online mailboxes using Outlook profiles that leveraged Basic Authentication. It supported common MAPI-over-HTTP and RPC-over-HTTP (Outlook Anywhere) protocols under this mechanism.
In such setups:
- Administrators could use MFCMAPI to explore mailbox folders, view MAPI properties, and delete problematic items.
- There was no dependency on token-based security or conditional access policies.
- MFCMAPI’s access was consistent and predictable, assuming Outlook itself could authenticate using stored credentials.
This compatibility made MFCMAPI a dependable utility for mailbox troubleshooting, especially in hybrid environments or during migrations to Office 365.
Microsoft’s Deprecation of Basic Authentication
In response to increasing cybersecurity threats and the need for more secure, flexible access protocols, Microsoft began phasing out Basic Authentication across Microsoft 365 and Exchange Online. This transition became effective in October 2022, when Microsoft disabled Basic Auth for several services, including MAPI, EWS, IMAP, POP, and SMTP AUTH.
As part of this initiative:
- Basic Authentication was disabled by default in new Microsoft 365 tenants.
- Existing tenants were progressively transitioned away from legacy protocols.
- Modern Authentication, based on OAuth 2.0 and backed by Azure AD, became the standard method for secure access.
This change has directly impacted tools like MFCMAPI that were previously compatible with environments using Basic Auth.
Limitations When Accessing Exchange Online Without Basic Auth
When Basic Authentication is disabled in Microsoft 365, MFCMAPI’s ability to interact with Exchange Online becomes limited and highly dependent on Outlook’s profile configuration. Specifically, the following limitations arise:
No Native OAuth Support in MFCMAPI
MFCMAPI does not have built-in support for Modern Authentication or OAuth token negotiation. It cannot prompt the user for Azure AD credentials, nor can it initiate an OAuth token request using MSAL (Microsoft Authentication Library). This is a critical limitation in today’s cloud-first environments.
Dependency on Outlook’s Authenticated Profile
Since MFCMAPI uses existing MAPI profiles, the only way it can access an Exchange Online mailbox in a Modern Auth-only environment is if Outlook itself is already configured for OAuth. This means:
- Outlook must have previously authenticated the user via Azure AD.
- The session must be live and authorized.
- Conditional Access and MFA (Multi-Factor Authentication) must be satisfied through Outlook before launching MFCMAPI.
In simple terms, MFCMAPI can “piggyback” on Outlook’s OAuth-authenticated session, but it cannot create one on its own.
No Visibility of Token Information
MFCMAPI has no UI or backend mechanism to show the OAuth access token, token expiration, or refresh cycle. This makes it difficult to troubleshoot OAuth issues directly within MFCMAPI, unlike tools that are designed to manage token flows explicitly.
Limited Functionality with Delegated Mailboxes
If an administrator attempts to use MFCMAPI to access another user’s mailbox (with delegate permissions), and that mailbox requires Modern Authentication, the tool may fail unless the delegate session was previously authenticated in Outlook using OAuth. This complicates scenarios involving shared or resource mailboxes.
Restricted Access in Secure Tenants
Many Microsoft 365 tenants have Conditional Access Policies that enforce specific login behaviors, such as device compliance, IP restrictions, or MFA requirements. Since MFCMAPI cannot meet or respond to these policies, it may fail to connect or display mailbox data, even if Outlook succeeds.
Impact on Troubleshooting Workflows
With the deprecation of Basic Authentication, many common use cases for MFCMAPI have become more restrictive. Tasks such as:
- Removing corrupt Outlook rules
- Deleting calendar items stuck in limbo
- Accessing the “Deletions” or “Substrate” folders
- Clearing out stuck read receipts
…may no longer be possible in the same way they were in Basic Auth environments. Admins now need to ensure that:
- MFCMAPI is being used with an Outlook profile that is already logged in via OAuth.
- The user’s session is active, and token expiration has not occurred.
- Any required permissions or policies are satisfied outside of MFCMAPI’s control.
This creates a more complex setup and often demands additional administrative coordination.
Recommendations for Admins and IT Professionals
To use MFCMAPI effectively in Modern Authentication environments, IT professionals should:
- Ensure Outlook is configured for OAuth
- Use the latest version of Outlook that supports Modern Authentication by default.
- Authenticate the Outlook Profile First
- Open Outlook, complete MFA, and ensure the mailbox is accessible.
- Avoid Relying on MFCMAPI for Login Prompts
- Since MFCMAPI cannot prompt for credentials or handle token refresh, always authenticate via Outlook.
- Understand Conditional Access Limitations
- If MFCMAPI fails to access a mailbox, it could be due to policies that it cannot comply with.
- Keep MFCMAPI Updated
- Use the latest builds from the developer to ensure compatibility with any changes to MAPI behavior.
Current State: Does MFCMAPI Support OAuth?
Overview of OAuth in the Microsoft Ecosystem
Modern Authentication, based on the OAuth 2.0 standard, is now the default authentication protocol for Microsoft 365 services, including Exchange Online. As Basic Authentication (username and password-based logins) continues to be phased out due to security concerns, organizations must ensure all applications interacting with Microsoft mail services are compatible with OAuth.
This shift has affected how administrators and developers access mailbox data, particularly through third-party tools or Microsoft’s diagnostic utilities such as MFCMAPI. Many are now asking: Does MFCMAPI support OAuth, and can it still function reliably in environments where Basic Authentication has been completely disabled?
To answer that, it’s necessary to understand how MFCMAPI works under the hood.
MFCMAPI’s Dependency on Extended MAPI and Outlook Profiles
MFCMAPI is a low-level diagnostic tool designed to expose the inner workings of a MAPI session. It does not operate as a full-fledged client like Microsoft Outlook, nor does it include its authentication infrastructure. Instead, MFCMAPI depends entirely on Extended MAPI—a legacy messaging API used by Outlook and other Microsoft applications to access messaging stores.
Because of this dependency, MFCMAPI does not perform direct authentication to mailboxes using its logic. It relies on existing Outlook profiles and the MAPI subsystem already configured on the system. In other words, MFCMAPI uses whatever authentication methods Outlook is already using. If Outlook is connected to a mailbox using OAuth 2.0, MFCMAPI can piggyback on that authenticated profile to access the mailbox data.
This architectural choice means MFCMAPI does not independently manage tokens or initiate OAuth flows. It also cannot open mailboxes directly using credentials or application permissions. Instead, it opens the mail profile through MAPI, and if that profile is already authenticated using Modern Authentication, access is granted.
MFCMAPI Does Not Natively Support OAuth Flows
It is important to understand the distinction between supporting OAuth and initiating OAuth flows. MFCMAPI does not support native OAuth prompts or token generation. It does not invoke a browser-based login screen or perform app-based OAuth client registration. These are essential parts of how typical applications perform OAuth authentication.
Since MFCMAPI does not include any of these components, it cannot directly prompt users for consent, acquire tokens, or perform refresh token operations. Instead, MFCMAPI works only in scenarios where the authentication has already occurred, primarily through a pre-configured Outlook profile that has completed the Modern Authentication process.
So, while MFCMAPI itself does not “support” OAuth in a direct or self-contained way, it can still access mailboxes authenticated via OAuth as long as it is operating through an Outlook profile that has already handled the OAuth handshake.
Requirement: Pre-Configured Outlook Profile with OAuth Enabled
For MFCMAPI to function properly in an environment where Basic Authentication has been disabled, you must first set up an Outlook profile that uses Modern Authentication.
Here’s what this involves:
- Use a supported version of Outlook that is capable of Modern Authentication (Outlook 2016 or later).
- Ensure OAuth is enabled at the tenant and application level in Microsoft 365 or Exchange Online settings.
- Configure the user profile in Outlook to connect to the mailbox. During this setup, Outlook will automatically use OAuth if it’s available and required.
- Complete the sign-in process within Outlook to cache the necessary access tokens.
- Once completed, this Outlook profile becomes usable by MFCMAPI for mailbox inspection.
MFCMAPI can then open the profile and access the mailbox using the existing authentication context. No additional login is required within MFCMAPI, and it never prompts for credentials or performs its token exchange. The tool essentially borrows the secure session already created and maintained by Outlook.
Why MFCMAPI Cannot Replace Outlook for OAuth Authentication
MFCMAPI lacks its identity platform integration, it cannot serve as a standalone client in OAuth environments. It doesn’t support integration with Microsoft Authentication Library (MSAL), Azure Active Directory (AAD) registration, or scope definition, which are required for any application seeking to natively implement OAuth 2.0.
MFCMAPI doesn’t have its method to securely store refresh tokens or access tokens. It cannot retrieve tokens from a cloud identity provider or manage consent and user delegation. This severely limits its ability to act independently of Outlook in cloud-first or security-hardened environments.
While some tools are beginning to incorporate OAuth token support using MSAL or Microsoft Graph API, MFCMAPI remains focused solely on its original purpose: low-level diagnostics and manual MAPI inspection using existing session contexts. It is not being developed into a standalone mail client with full OAuth capabilities.
Practical Implications for IT Administrators and Support Teams
For administrators and engineers working in modern environments, this limitation means that MFCMAPI remains usable, but only under specific conditions:
- The user must already be signed into Outlook with Modern Authentication.
- The Outlook profile must be available and functional on the local machine.
- MFCMAPI must be launched in a session that has access to this profile.
- The machine must maintain connectivity and access to cached tokens or authentication contexts managed by Outlook.
If Basic Authentication has been disabled and no Outlook profile using OAuth is available, MFCMAPI will not be able to connect to the mailbox. In such cases, MFCMAPI will throw errors or fail to resolve MAPI stores due to authentication failure.
This means that MFCMAPI cannot be used for account recovery or mailbox access unless the correct Outlook profile and credentials are already configured and authenticated.
Workarounds and Requirements for Using MFCMAPI with Modern Authentication (OAuth)
As Microsoft continues to phase out Basic Authentication across its Exchange Online services, many administrators and support professionals who rely on legacy tools such as MFCMAPI are faced with a growing concern: How can they continue using these tools in environments where only Modern Authentication (OAuth 2.0) is permitted? While MFCMAPI does not natively support OAuth in a standalone capacity, there are strategic workarounds that enable its continued use within OAuth-secured environments, primarily through the integration with properly configured Outlook profiles.
This section provides an in-depth explanation of the practical requirements and functional workarounds necessary to operate MFCMAPI securely and effectively when Modern Authentication is enforced.
Prerequisite: Install Outlook with Modern Authentication Configured
The first and most important requirement is the installation of Microsoft Outlook that is configured to use Modern Authentication. This configuration is vital because MFCMAPI does not possess its authentication mechanism — instead, it relies entirely on the existing Outlook profile for access.
Modern Authentication must already be enabled and operational within the Outlook application. This is typically managed through the Office 365 Admin Center or via Group Policy settings and registry keys on Windows. When correctly configured, Outlook uses OAuth tokens to securely authenticate to Exchange Online without transmitting the user’s username and password directly.
In practice, this means the following:
- Your version of Outlook must support OAuth: Versions beginning with Outlook 2013 (with updates) and higher support Modern Authentication.
- OAuth must be enabled in your Office 365 tenant or Exchange environment: This often involves checking that Modern Authentication has been turned on for the organization.
- Registry keys may need to be adjusted: On some systems, registry modifications are required to explicitly enable OAuth for Office applications.
Without this proper configuration, any attempts to access the mailbox through MFCMAPI will fail when Basic Authentication has been disabled, because MFCMAPI cannot independently prompt the user to log in through an OAuth token exchange process.
Use an Already-Authenticated Outlook Profile with OAuth
Once Outlook has been installed and Modern Authentication is working, the next essential requirement is to create and use an Outlook profile that has already been authenticated using OAuth. This is the most practical workaround that allows MFCMAPI to function in Modern Authentication environments.
Here’s how this process works:
- The user logs in to Outlook, and the client securely authenticates using OAuth.
- Once authenticated, an MAPI profile is established and stored on the system.
- This Outlook profile contains all the necessary connection data and tokens required to access the mailbox through MAPI.
- MFCMAPI is then launched and directed to use this already-authenticated profile.
- MFCMAPI inherits the authenticated context and can open the mailbox, browse folders, and perform diagnostic actions without requiring any additional login steps.
It is important to note that MFCMAPI cannot create or authenticate a profile itself. It does not contain any code or mechanism to handle OAuth token acquisition, refresh, or expiration. Therefore, it must depend entirely on the authentication already completed by Outlook.
This method works well for most administrative tasks when performed shortly after Outlook authentication. If the authentication token expires or the session times out, the Outlook profile may require re-authentication before MFCMAPI can continue functioning correctly.
MFCMAPI cannot Authenticate Standalone via OAuth
One of the most common misconceptions about MFCMAPI is that it might be capable of initiating its authentication process, especially with the growing industry shift toward Modern Authentication. However, MFCMAPI is not a standalone OAuth-capable application. It was not designed to support token-based authentication or integrate with Microsoft’s identity platform (e.g., Azure AD, MSAL).
This limitation means:
- MFCMAPI does not support login prompts using OAuth flows.
- It cannot register as an application in Azure AD or obtain client IDs for token issuance.
- It lacks the user interface or backend code needed to perform OAuth redirects, consent, or multi-factor authentication (MFA).
- It cannot function in environments that require OAuth unless a previously authenticated profile is available.
Because of these constraints, any attempt to use MFCMAPI in a pure OAuth-only tenant without a valid Outlook profile will result in errors such as “Access Denied” or failure to initialize the MAPI session. If Basic Authentication has been completely disabled at the tenant level and no Outlook OAuth profile is available, MFCMAPI will become effectively unusable.
This makes it critical for support staff to understand that MFCMAPI is a dependent tool, not a self-sufficient client. It relies on the system configuration and authenticated session tokens provided by Outlook, which itself acts as the front-end for user authentication.
Best Practices for MFCMAPI in OAuth-Enforced Environments
To maximize success when using MFCMAPI in modern, secure environments, consider the following best practices:
- Always authenticate Outlook before launching MFCMAPI: Ensure that the Outlook profile is logged in and functional.
- Use the same Windows session for both Outlook and MFCMAPI: MFCMAPI operates within the user context, so switching accounts or sessions may break the token chain.
- Avoid running MFCMAPI on shared or public machines: OAuth tokens may not persist or may conflict across user sessions.
- Test OAuth profile access in Outlook before troubleshooting: If Outlook cannot connect, MFCMAPI will not be able to either.
- Maintain up-to-date versions of both Outlook and MFCMAPI: While MFCMAPI does not handle OAuth natively, newer builds may improve stability and compatibility with evolving Outlook versions.
- Re-authenticate Outlook periodically: This ensures that access tokens are refreshed and remain valid for diagnostic tools that depend on them.
Limitations and Known Issues in MFCMAPI’s Support for Modern Authentication
As the transition from legacy Basic Authentication to Modern Authentication (OAuth 2.0) becomes standard across Microsoft 365 services, tools like MFCMAPI are also under scrutiny regarding their compatibility with modern security requirements. While MFCMAPI remains an essential utility for Exchange and Outlook mailbox diagnostics, its limitations in fully supporting OAuth have introduced operational challenges, especially in cloud-based environments such as Exchange Online.
In this section, we will explore the core limitations and known issues that arise when using MFCMAPI in an OAuth-enabled environment, including problems with Exchange Online access, the absence of built-in token authentication mechanisms, and the lack of native support for Microsoft Authentication Library (MSAL).
Challenges in Accessing Exchange Online with Improper OAuth Configuration
One of the most prominent limitations users encounter is the inability to access Exchange Online if Modern Authentication is not properly configured. This challenge stems from how MFCMAPI interacts with Outlook profiles and the underlying MAPI subsystem.
No Direct Authentication Mechanism
MFCMAPI does not include its built-in authentication engine. Instead, it relies entirely on the default Outlook profile settings and the authentication methods configured therein. If the Outlook profile is not already set up with Modern Authentication, or if the OAuth tokens have expired, MFCMAPI will fail to establish a connection to the mailbox.
Basic Authentication Deprecation
As Microsoft continues to deprecate Basic Authentication in Exchange Online, users who once depended on username and password prompts will no longer be able to connect. For environments that have disabled Basic Auth completely, MFCMAPI becomes non-functional unless Modern Authentication is configured through Outlook.
Profile Dependency
Even in cases where Outlook is installed, if the user has not signed in using an account that supports OAuth or the token has expired, MFCMAPI cannot access the mailbox. This creates a critical limitation: administrators must ensure that the Outlook profile is not only present but also authenticated via OAuth before attempting to use MFCMAPI.
Absence of Built-in Token Prompt or OAuth UI
Another critical drawback is that MFCMAPI does not provide any built-in interface or prompt for Modern Authentication. Most modern Microsoft 365 apps, including Outlook, Microsoft Teams, and OneDrive, use MSAL or ADAL (Active Directory Authentication Library) to initiate OAuth flows, prompting users to log in via a browser or secure modal window. MFCMAPI, however, lacks this functionality.
No Interactive Login Flow
Modern Authentication typically involves an interactive login process where users are redirected to a Microsoft login page to authenticate and authorize access. MFCMAPI does not initiate this process. It does not display any login window, nor does it request or store tokens. As a result, it cannot obtain the access tokens required for connecting to OAuth-enabled mailboxes on its own.
Silent Failures
This limitation also introduces silent failure scenarios. When a user tries to connect to a mailbox via MFCMAPI using a profile that is not OAuth-compliant, the tool may simply fail to connect without giving an informative error related to authentication. This leads to confusion, especially among IT professionals troubleshooting mailboxes in cloud or hybrid environments.
Manual Workarounds Required
To successfully use MFCMAPI in an OAuth-only environment, users must first log in through Outlook using the desired account. This ensures that the access tokens are generated and cached by Outlook. Only then can MFCMAPI “piggyback” on the authenticated session using the existing MAPI profile. This workaround is far from ideal, particularly in enterprise environments where access is tightly controlled and scripting or automation is needed.
Lack of Native Microsoft Authentication Library (MSAL) Integration
Microsoft Authentication Library (MSAL) is the recommended way to implement Modern Authentication across Microsoft applications and services. MSAL handles token acquisition, secure credential storage, token refresh, and interactive logins. Unfortunately, MFCMAPI does not natively integrate with MSAL, further limiting its ability to support secure access.
No Token Lifecycle Management
Without MSAL, MFCMAPI cannot manage the token lifecycle. It cannot:
- Acquire new access or refresh tokens.
- Automatically refresh expired tokens.
- Perform silent authentication using cached credentials.
- Access secure resources via scopes and consent.
This means that MFCMAPI is entirely dependent on the Outlook client to manage authentication, significantly reducing its independence as a diagnostic tool in modern environments.
Security and Compliance Gaps
Modern security standards emphasize token-based authentication with least privilege access. Because MFCMAPI lacks MSAL support, it cannot enforce or comply with conditional access policies, multi-factor authentication (MFA), or scope-specific token requests. This makes it less viable for use in secure enterprise networks where these policies are strictly enforced.
Limitations for Developers and Advanced Users
For developers or IT administrators who want to extend MFCMAPI’s functionality — such as automating mailbox access or integrating with secure cloud services — the absence of MSAL integration is a significant obstacle. There is currently no way to programmatically inject a valid token or authorize MFCMAPI through OAuth endpoints without relying on external tools or manually authenticated profiles.
Practical Implications of These Limitations
Understanding these constraints is crucial for professionals working with Exchange Online or hybrid mail systems. The most common implications include:
- Inability to troubleshoot cloud-based mailboxes if Modern Authentication is enforced.
- Dependency on local Outlook profiles, which adds setup complexity.
- Manual pre-authentication is required, which prevents automation and scripting.
- No support for conditional access or MFA, making MFCMAPI unsuitable in high-security environments.
- Confusing behavior during failed logins often requires deep technical knowledge to diagnose.
Temporary Workarounds
While these limitations are significant, some workarounds exist:
- Pre-authenticate via Outlook: Sign into Outlook using an OAuth-compliant account before launching MFCMAPI.
- Use local profiles only: Ensure the desired profile is locally available and connected.
- Avoid cloud mailboxes where Basic Auth is disabled: For full access, MFCMAPI is best suited to on-premises Exchange or hybrid systems with Basic Authentication still available.
These are not permanent solutions and may stop working as Microsoft enforces stricter authentication across all services.
Future Outlook and Development of MFCMAPI’s OAuth Support
As Microsoft continues to strengthen the security landscape of its cloud and messaging platforms, the use of Modern Authentication (OAuth 2.0) has become not just a recommendation but a requirement, especially for organizations using Exchange Online and Microsoft 365. With the deprecation of Basic Authentication across many Microsoft services, tools like MFCMAPI are under increasing scrutiny for their ability—or lack thereof—to operate in OAuth-only environments.
This section explores the current state of MFCMAPI’s OAuth integration, the developer community’s response, and any visible roadmap or potential direction for future enhancements.
The Developer’s Stance: No Native OAuth Support Yet
As of the most recent stable builds, MFCMAPI does not offer native OAuth 2.0 (Modern Authentication) support. This means the tool itself cannot independently initiate OAuth login flows or integrate directly with Microsoft Identity platforms using ADAL or MSAL libraries. Instead, MFCMAPI relies on Outlook profiles, which must already be authenticated using Modern Authentication in the background.
The MFCMAPI tool, developed and maintained by Stephen Griffin, a Microsoft engineer, is available publicly on GitHub. While it is maintained to support critical functionality and compatibility with newer versions of Outlook and Exchange, it is important to note that this is not a full-time product or a commercial solution. Therefore, the inclusion of complex features like native OAuth support is not guaranteed, nor is there an official development roadmap outlining such plans.
Outlook Profiles as a Temporary Workaround
Currently, the most effective workaround for using MFCMAPI in an OAuth-only environment is to ensure the Outlook profile being used has already been authenticated via Modern Authentication. When MFCMAPI accesses this profile, it leverages the session context and authentication tokens already granted through Outlook.
This workaround is sufficient in many enterprise environments. However, it introduces limitations for administrators who:
- Want to connect to Exchange Online without an Outlook installation?
- Use shared mailboxes, service accounts, or accounts without GUI-based profile configuration.
- Work in automated or headless diagnostic environments.
These constraints underscore the growing need for MFCMAPI or alternative tools to include native OAuth support, rather than depending on Outlook’s session handling.
Community Discussions and Feature Requests on GitHub
The open-source nature of MFCMAPI has led to several discussions within the GitHub community around the feasibility and necessity of Modern Authentication support. While the repository does not reflect a formal roadmap, issues and enhancement requests related to OAuth are frequently submitted and discussed.
Common themes in these discussions include:
- Requests to integrate MSAL.NET, Microsoft’s modern authentication library, into MFCMAPI.
- Suggestions for enabling token-based sign-in mechanisms.
- Reports of authentication failures when organizations enforce OAuth-only policies.
- Inquiries about workarounds and registry-level tweaks to force Outlook to use OAuth.
To date, responses from the project maintainer have generally acknowledged the importance of Modern Authentication but also highlighted the significant architectural changes required to integrate OAuth. The tool is heavily dependent on Extended MAPI, a COM-based legacy API that predates Modern Authentication. As a result, integrating OAuth would involve a complex overhaul of both the authentication process and the user interface to accommodate token management and sign-in flows.
MSAL Integration: Challenges and Considerations
The most straightforward method to bring OAuth support into MFCMAPI would be via the integration of MSAL (Microsoft Authentication Library). However, this is far from trivial. Here are a few reasons why:
- Token Management: MFCMAPI would need to handle access tokens, refresh tokens, and expiration logic—functionality it currently does not support.
- User Consent and Sign-In UI: OAuth requires a user interface to allow sign-in, grant consent, and handle redirects. MFCMAPI is not designed for interactive workflows.
- Profile-Independent Access: OAuth-based access would imply profile-less mailbox connections, requiring deeper support for Exchange Web Services (EWS) or Graph API, which are outside the current MAPI architecture of MFCMAPI.
Due to these limitations, the community is divided between enhancing MFCMAPI versus building an entirely new diagnostics tool using modern APIs such as Microsoft Graph, which natively support OAuth.
The Role of Microsoft Graph and Outlook REST APIs
Another forward-looking approach discussed among developers is the transition toward using the Microsoft Graph API for diagnostics and mailbox analysis. Microsoft Graph is a RESTful web API that provides secure and OAuth-compliant access to Microsoft 365 data.
Unlike MFCMAPI, Microsoft Graph:
- Natively supports Modern Authentication and application-level permissions.
- Works without a locally configured Outlook profile.
- It is scalable, secure, and better aligned with Microsoft’s long-term architecture.
Some community contributors and Microsoft MVPs have started building custom PowerShell scripts and lightweight tools using Graph to mimic the functionality of MFCMAPI. While these tools are still in development or serve limited use cases, they hint at a potential next-generation alternative to MFCMAPI that is cloud-native and OAuth-ready by design.
Recommendations for the Present and the Future
Until native OAuth support is introduced in MFCMAPI (if ever), IT professionals and developers are advised to:
- Use Outlook profiles configured with Modern Authentication to access mailboxes via MFCMAPI.
- Stay informed via the tool’s GitHub repository for any updates or new builds.
- Contribute to or support feature discussions to express demand for OAuth capabilities.
- Consider alternative tools or scripts that use Microsoft Graph for read-only diagnostics.
Organizations that have already disabled Basic Authentication across Exchange Online must ensure their MFCMAPI use cases align with these limitations, especially when handling compliance, security audits, or mailbox migrations.
Conclusion
MFCMAPI continues to be an indispensable tool for deep-level mailbox diagnostics and troubleshooting in Outlook and Exchange environments. However, as the Microsoft ecosystem evolves toward stricter security and compliance standards, especially with the widespread enforcement of Modern Authentication (OAuth 2.0), the tool faces notable limitations. Currently, MFCMAPI does not support native OAuth flows and relies heavily on Outlook profiles that have already authenticated using Modern Authentication.
While discussions within the developer community and on GitHub reflect interest in future enhancements, there is no confirmed roadmap or timeline for integrating OAuth directly into MFCMAPI. The architectural complexities and reliance on legacy MAPI frameworks make such a transition challenging. For now, administrators must continue using configured Outlook profiles as a workaround and remain vigilant for updates or alternative tools that align with modern authentication standards.